When it comes to
interconnecting a private network (whether corporate or private) in IPv4, it is
virtually impossible to do without NAT. Here is a configuration that takes up the essentials of the three
main types of NAT that can be configured, namely:
- Static NAT
- Dynamic NAT with address pool
- Dynamic NAT with overload (NAT overload, also known as PAT)
Topology of the lab
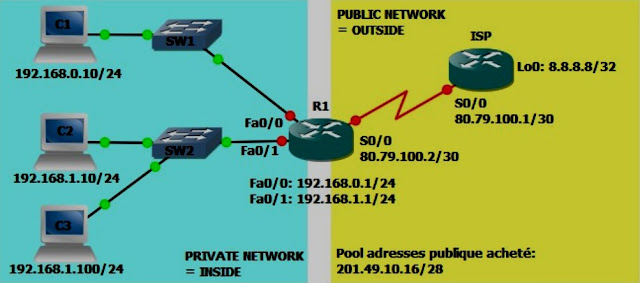 |
| NAT Topology |
The lab is divided into two
parts, the private side (company network) and the public side (the ISP and the
Internet). The ISP router (which
represents the ISP), has no knowledge of the company's private networks and
therefore cannot route anything to the 192.168.xx networks. These addresses are reserved
for use in private networks. The same applies to all
addresses in the following ranges:
- 10.0.0.0/8 (from 10.0.0.0 to 10.255.255.255)
- 172.16.0.0/12 (from 172.16.0.0 to 172.31.255.255)
- 192.168.0.0/16 (from 192.168.0.0 to 192.168.255.255)
We will then configure the NAT
to allow access to the Internet (simulated by address 8.8.8.8/32 configured on
a loopback interface of ISP):
- The 192.168.0.0/24 network will use dynamic NAT with overload.
- The 192.168.1.0/24 network will use NAT with address pool.
- The 192.168.1.100 machine will be accessible from the public network through a static NAT configuration.
Configuring the Basic Topology
On ISP:
Configuring the loopback
interface
ISP#conf t
ISP(config)#int l0
ISP(config-if)#ip address 8.8.8.8 255.255.255.255
ISP(config-if)#exit
Configuring the serial link to
R1
ISP(config)#int s0/0
ISP(config-if)#no shut
ISP(config-if)#ip address 80.79.100.1 255.255.255.252
ISP(config-if)#exit
Configuring the route to the
public address pool
ISP(config)#ip route 201.49.10.16 255.255.255.240 serial 0/0
About R1
Configuring the serial
interface to ISP
R1#conf t
R1(config)#int s0/0
R1(config-if)#ip address 80.79.100.2 255.255.255.252
R1(config-if)#no shut
R1(config-if)#exit
Configuring the LAN1 Interface
R1(config)#int fa0/0
R1(config-if)#ip address 192.168.0.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#exit
Configuring the LAN2 Interface
R1(config)#int fa0/1
R1(config-if)#ip address 192.168.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#exit
Setting the default route
R1(config)#ip route 0.0.0.0 0.0.0.0 serial 0/0
For the moment it is possible
to carry out the following tests:
- Ping from each PC to R1
- Ping between different LAN PCs
- Ping from R1 to 8.8.8.8
Test from C1 to R1
VPCS[1]> ping 192.168.0.1
192.168.0.1 icmp_seq=1 ttl=255 time=70.000 ms
192.168.0.1 icmp_seq=2 ttl=255 time=54.000 ms
192.168.0.1 icmp_seq=3 ttl=255 time=67.000 ms
192.168.0.1 icmp_seq=4 ttl=255 time=65.000 ms
192.168.0.1 icmp_seq=5 ttl=255 time=63.000 ms
Test from C1 to C2
VPCS[1]> ping 192.168.1.10
192.168.1.10 icmp_seq=1 ttl=63 time=31.000 ms
192.168.1.10 icmp_seq=2 ttl=63 time=16.000 ms
192.168.1.10 icmp_seq=3 ttl=63 time=32.000 ms
192.168.1.10 icmp_seq=4 ttl=63 time=32.000 ms
192.168.1.10 icmp_seq=5 ttl=63 time=32.000 ms
Testing R1 to 8.8.8.8
R1#ping 8.8.8.8
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 8.8.8.8, timeout is 2 seconds:
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 1/29/112 ms
On the other hand impossible
for example for C1 to communicate with 8.8.8.8
VPCS[1]> ping 8.8.8.8
8.8.8.8 icmp_seq=1 timeout
8.8.8.8 icmp_seq=2 timeout
8.8.8.8 icmp_seq=3 timeout
8.8.8.8 icmp_seq=4 timeout
8.8.8.8 icmp_seq=5 timeout
Common configuration for any
type of NAT
The first thing to do when
configuring NAT, regardless of the type, is to tell the router where the
private network is located and where the public network is located.
NAT takes effect only when a
packet is routed from an "inside" (private side) interface to an
"outside" (public side) interface and vice versa.
In our case, the interfaces Fa0
/ 0 and Fa0 / 1 are on the private side and will be declared as
"inside", the interface S0 / 0 on the other hand, being on the public
side, will be configured as "outside".
R1(config)#int fa0/0
R1(config-if)#ip nat inside
R1(config-if)#exit
R1(config)#int fa0/1
R1(config-if)#ip nat inside
R1(config-if)#exit
R1(config)#int s0/0
R1(config-if)#ip nat outside
R1(config-if)#exit
Configuring Static NAT for C3
What we are going to configure
here is a static translation in the translation table NAT, which is commonly
called on domestic hardware "open a port". We will explicitly tell the
router that what happens on its public interface (S0 / 0) and whose destination
address is 201.49.10.30 (one of the public pool address) must be redirected to
192.168.1.100.
From the router's point of
view, this amounts to modifying the IP address of the request in the IPv4
header before routing the packet. This also means that if C3 sends a packet to the Internet, at the
output of S0 / 0 of R1 the source address (192.168.1.100) will be replaced by
the address specified in the translation, that is 201.49.10.30.
R1(config)#ip nat inside source static 192.168.1.100 201.49.10.30
The NAT translations table must
now look like this:
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
--- 201.49.10.30 192.168.1.100 --- ---
R1#
Now C3 must be able to
communicate with the public network
VPCS[3]> ping 8.8.8.8
8.8.8.8 icmp_seq=1 ttl=254 time=119.000 ms
8.8.8.8 icmp_seq=2 ttl=254 time=102.000 ms
8.8.8.8 icmp_seq=3 ttl=254 time=75.000 ms
8.8.8.8 icmp_seq=4 ttl=254 time=117.000 ms
8.8.8.8 icmp_seq=5 ttl=254 time=116.000 ms
Each packet has therefore been
translated, proof is the table of translations just after the emission of these
pings:
R1#show ip nat translations
Pro Inside global Inside local Outside local Outside global
icmp 201.49.10.30:33598 192.168.1.100:33598 8.8.8.8:33598 8.8.8.8:33598
icmp 201.49.10.30:33854 192.168.1.100:33854 8.8.8.8:33854 8.8.8.8:33854
icmp 201.49.10.30:34366 192.168.1.100:34366 8.8.8.8:34366 8.8.8.8:34366
icmp 201.49.10.30:34622 192.168.1.100:34622 8.8.8.8:34622 8.8.8.8:34622
icmp 201.49.10.30:34878 192.168.1.100:34878 8.8.8.8:34878 8.8.8.8:34878
--- 201.49.10.30 192.168.1.100 --- ---
R1#
One can observe the result of
translation on the side of ISP also using the command "debug ip
packet" which will display the detail of each IP packet processed by the
router (Attention, in a real environment this command can seriously saturate
The router).
ISP#debug ip packet
*Mar 1 02:22:49.491: IP: tableid=0, s=201.49.10.30 (Serial0/0), d=8.8.8.8 (Loopback0), routed via RIB
*Mar 1 02:22:49.491: IP: s=201.49.10.30 (Serial0/0), d=8.8.8.8, len 92, rcvd 4
*Mar 1 02:22:49.495: IP: tableid=0, s=8.8.8.8 (local), d=201.49.10.30 (Serial0/0), routed via FIB
*Mar 1 02:22:49.495: IP: s=8.8.8.8 (local), d=201.49.10.30 (Serial0/0), len 92, sending
Configuring NAT with Address Pool
For now only C3 has access to
the public network, we will now configure another type of NAT for network
192.168.1.0/24 (except for C3).
Here, instead of configuring a
static translation, we will give the router a range of public addresses (an
address pool) in which it can draw to dynamically create the translations.
First create the address pool
R1(config)#ip nat pool POOL-NAT-LAN2 201.49.10.17 201.49.10.30 netmask 255.255.255.240
Here, therefore, an address
range named POOL-NAT-LAN2 is created, ranging from 201.49.10.17 to
201.49.10.30.
We then have to define which IP
addresses are likely to be translated ... for this we must create an ACL.
R1(config)#access-list 1 deny 192.168.1.100
R1(config)#access-list 1 permit 192.168.1.0 0.0.0.255
It is therefore possible to
translate the ip addresses of the network 192.168.1.0/24 except 192.168.1.100
(for which we already have a static translation).
It only remains to configure
the NAT in itself
R1(config)#ip nat inside source list 1 pool POOL-NAT-LAN2
The router is hereby instructed
to dynamically create a translation for packets arriving on an
"inside" interface routed through an "outside" interface
whose source IP address corresponds to the ACL 1 and to replace the source IP
with one of Those included in the POOL-NAT-LAN2 pool.
Note that if there is more
machine in the private network than public addresses available, then the
keyword "overload" must be added to the command:
R1(config)#ip nat inside source list 1 pool POOL-NAT-LAN2 overload
This makes it possible to
"share" the public addresses by also translating the port numbers in
the header of the transport layer (method commonly called PAT).
At present C2 (and the other
machines that would be in the network 192.168.1.0/24) can communicate with the
outside.
VPCS[2]> ping 8.8.8.8
8.8.8.8 icmp_seq=1 ttl=254 time=111.000 ms
8.8.8.8 icmp_seq=2 ttl=254 time=97.000 ms
8.8.8.8 icmp_seq=3 ttl=254 time=143.000 ms
8.8.8.8 icmp_seq=4 ttl=254 time=131.000 ms
8.8.8.8 icmp_seq=5 ttl=254 time=99.000 ms
The translation table of R1 now
has a new entry created dynamically, but it reserves the public address for C2
(as long as the NAT table is not purged).
R1#sh ip nat trans
Pro Inside global Inside local Outside local Outside global
--- 201.49.10.17 192.168.1.10 --- ---
--- 201.49.10.30 192.168.1.100 --- ---
R1#
Configuration of dynamic NAT
with overload (without pool)
It is still necessary to
configure R2 so that the network 192.168.0.0/24 can access the outside. For this we will configure the
third type of NAT, namely dynamic NAT with overloading using the public address
configured on the S0 / 0 interface of R1.
Note that this is the most
common configuration in a modest network (for example, in a home network). This method does not require
obtaining new public addresses from the provider.
This time we also need to
identify the source addresses to pass through the NAT, so we create a new ACL.
R1(config)#access-list 2 permit 192.168.0.0 0.0.0.255
All you need to do is configure
NAT.
R1(config)#ip nat inside source list 2 interface serial 0/0 overload
Here we say to the router to
translate the packets from the addresses described in ACL 2 (192.168.0.0/24)
and to replace the source IP address with that configured on the Serial 0/0
interface by overloading it to allow More than one machine to communicate with
the outside (PAT).
C1 (and any machine in this
network) can communicate with the outside world
VPCS[1]> ping 8.8.8.8
8.8.8.8 icmp_seq=1 ttl=254 time=132.000 ms
8.8.8.8 icmp_seq=2 ttl=254 time=130.000 ms
8.8.8.8 icmp_seq=3 ttl=254 time=127.000 ms
8.8.8.8 icmp_seq=4 ttl=254 time=112.000 ms
8.8.8.8 icmp_seq=5 ttl=254 time=125.000 ms
The debug ip packets on ISP
gives the following result
ISP#
*Mar 1 03:11:46.195: IP: tableid=0, s=80.79.100.2 (Serial0/0), d=8.8.8.8 (Loopback0), routed via RIB
*Mar 1 03:11:46.195: IP: s=80.79.100.2 (Serial0/0), d=8.8.8.8, len 92, rcvd 4
*Mar 1 03:11:46.199: IP: tableid=0, s=8.8.8.8 (local), d=80.79.100.2 (Serial0/0), routed via FIB
*Mar 1 03:11:46.199: IP: s=8.8.8.8 (local), d=80.79.100.2 (Serial0/0), len 92, sending
We see here that it is the
address of S0 / 0 that is used to replace the source IP of the packet.
0 comments:
Post a Comment